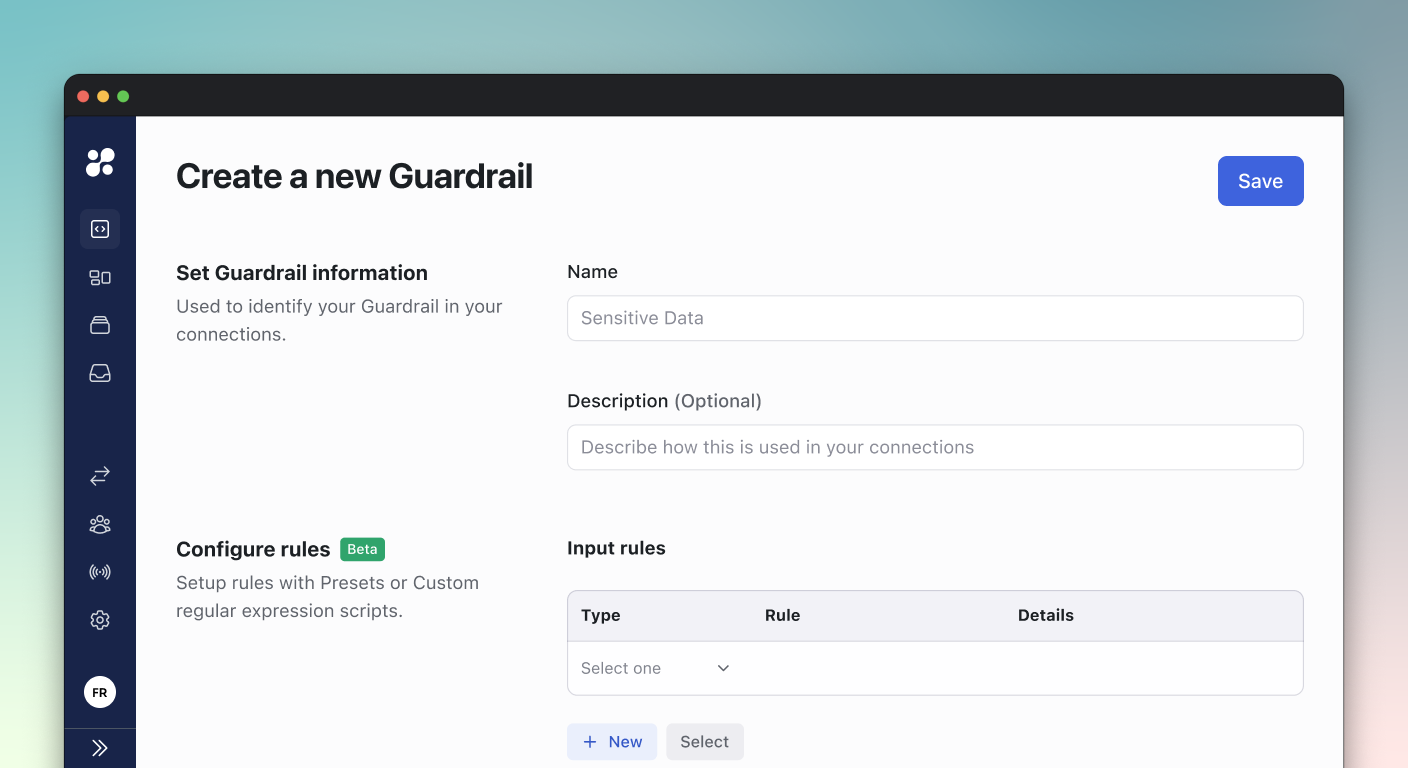
Creating a Guardrail
Configuring Rules
Input Rules
Rules that evaluate incoming commands or queries:- Pattern Matching: Define patterns to match specific commands or queries
- Conditions: Set conditions that trigger the rule
Output Rules
Rules that control or modify the output of commands:- Information Control: Control what information can be returned
Rule Types
Pattern Rules
Pattern Rules
Create rules based on command or query patterns:
- Regular expressions
- Exact matches
- Wildcard patterns
Security Rules
Security Rules
Enforce security policies:
- Block dangerous commands
- Require additional approvals
- Limit access to sensitive data
Compliance Rules
Compliance Rules
Ensure compliance requirements:
- Data access restrictions
- Audit logging requirements
- Regulatory compliance rules
Applying Guardrails
Connection Assignment
Best Practices
Start Simple
Begin with basic rules and expand as needed
Test Rules
Validate rules in a test environment first
Document Purpose
Clearly describe what each rule does
Regular Review
Periodically review and update rules

